As businesses increasingly rely on SaaS (Software-as-a-Service) applications, cybersecurity threats have evolved. Now in 2025, it’s crucial to adopt the SaaS security measures. In 2025, SaaS platforms are going to face more advanced cyberattacks, and hence, the necessity for better security practices is imperative. This blog explores the practice of cyber security for SaaS applications in 2025 to protect sensitive data and mitigate risks.
In this blog, Let’s get to know the fundamentals first, such as – what is SaaS data security? which is a SaaS Security platform? and other related terms.
What is SaaS Security?
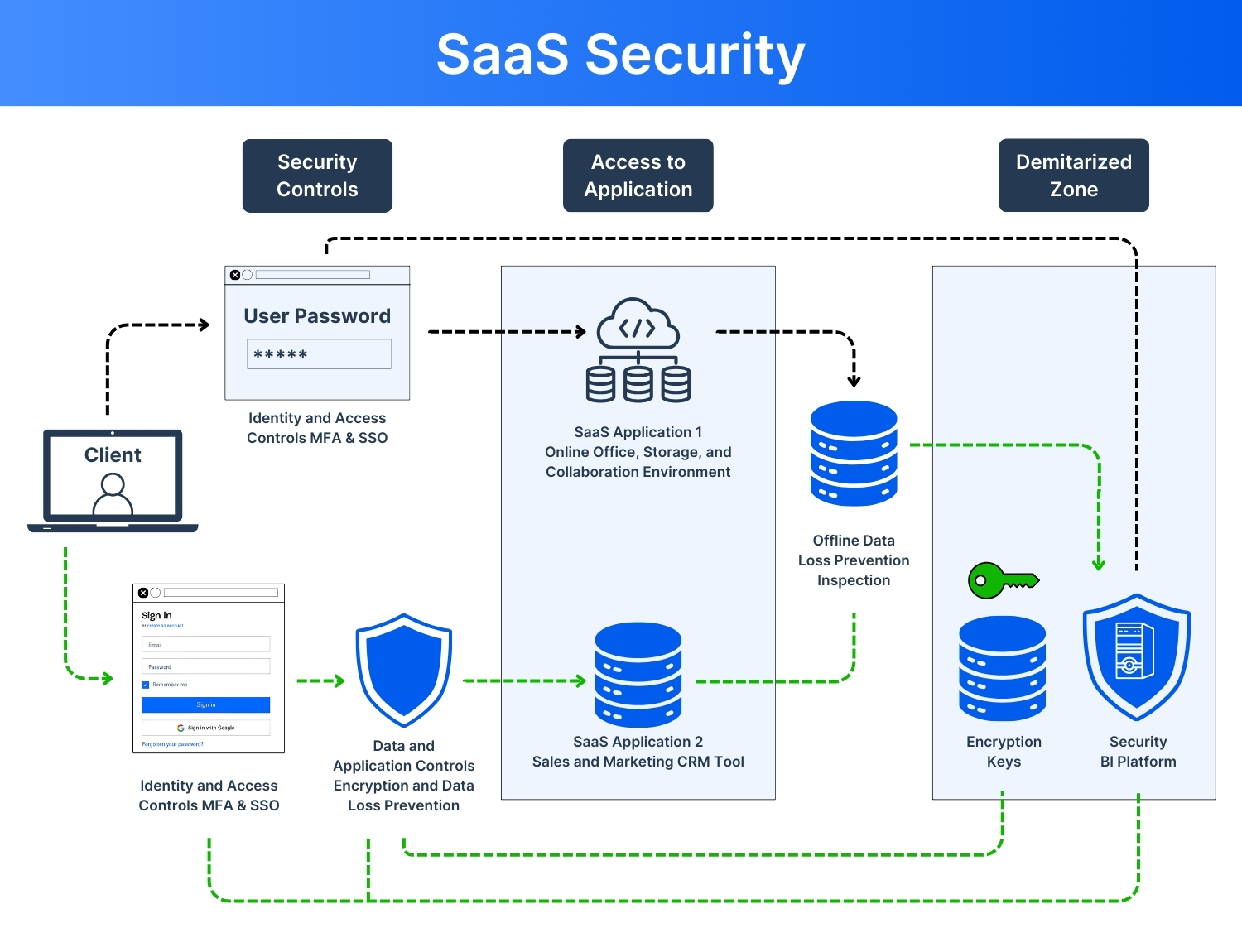
SaaS Data Security is the collection of practices, policies, and technology intended for SaaS data protection and to preserve their data from cyber-attacks, unauthorized access, data breaches, and compliance risks. Because SaaS applications are hosted in the cloud and accessed through the internet, they need robust measures to protect confidential data and maintain business continuity.
Why Is SaaS Security Becoming a Growing Concern?
SaaS applications have become very critical to businesses as they allow remote work, simple scaling, and frictionless collaboration. That being said, this ease of use comes with security threats as well.
Since SaaS platforms store sensitive data for multiple users and companies, they are attractive targets for hackers. Many SaaS applications are connected with other tools & create complex systems that can increase security risks.
Some of the major risks include SaaS breaches, which can expose important data. For this, companies need to implement SaaS cyber security best practices to safeguard against cyber threats, unauthorized access, and data leaks. In this blog, we will explore the security challenges and cyber security practices that helps you to protect your SaaS application.
The Security Challenges of SaaS Applications
Most SaaS software users have sensitive data that is involuntarily exposed on the internet at some point, resulting from configuration issues and weak data protection strategies.
SaaS applications frequently give companies a competitive advantage. SaaS provides scalability and agility, but companies also need to address security issues and implement measure to reduce risks.
- Lack of definition of SaaS ownership.
- There are too many privileged users.
- Scarcity security acumen.
- Unchecked updates from SaaS providers.
These factors make SaaS environments less secure for businesses. While not all companies have in-house security teams, SaaS security companies help improve protection.
10 Best Practices Of Cyber Security For SaaS Applications in 2025
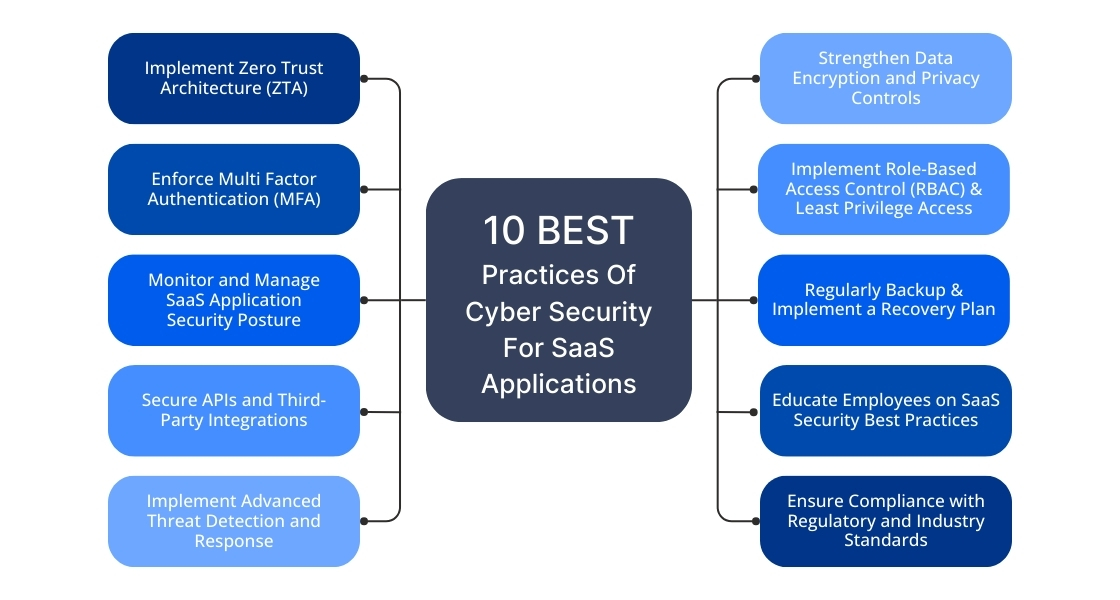
To mitigate these data breach risks and strengthen SaaS security, organizations should adopt the cyber security trends with the following best SaaS security solutions:
1. Implement Zero Trust Architecture (ZTA)
With cyber threats becoming more complex, Zero Trust Security has become a fundamental approach for SaaS application security.
Key Principles of Zero Trust:
- Never trust, always verify: Every request is authenticated and authorized before access is granted.
- Least privilege access: Users and apps are granted only the permissions they absolutely require.
- Micro-segmentation: Prevents lateral attacks by limiting movement within the network.
Why It’s Important:
Perimeter-based SaaS security models are no longer adequate, as remote work and cloud-based computing increase the attack surface. ZTA allows even if attackers obtain initial access, they cannot move freely within the system. By demanding strict authentication and monitoring, ZTA reduces the chances of data breach.
2. Enforce Multi Factor Authentication (MFA)
Password-based security is no longer sufficient. MFA makes security stronger by needing more than one way to confirm identity.
Factors such as:
- Something you know (password or PIN)
- Something you have (smartphone or security token)
- Something you are (biometrics like fingerprint or other things like iris or facial recognition)
Why It’s Important:
Cybercriminals typically use credential-stuffing attacks to target weak or reused passwords. Multi factor authentication methods effectively minimize the risk of unauthorized access even when a password is hacked. Numerous regulatory policies, including GDPR and SOC 2, now require MFA as part of their security best practices.
3. Monitor and Manage SaaS Application Security Posture
Best Practices:
- Conduct regular security audits.
- Use Cloud Access Security Brokers (CASBs) to monitor SaaS security.
- Automate detection and remediation of security misconfigurations.
Why It’s Important:
Most of the security violations are caused by cloud-based SaaS applications’ misconfigurations. Without continuous monitoring, these vulnerabilities remain undetected for months. As per the best practice of cyber security for Saas application, SPM tool implementation ensures that organizations have excellent security hygiene and can easily spot anomalies before they become significant incidents.
4. Secure APIs and Third-Party Integrations
SaaS solutions are dependent on APIs for integrating other services. It is important to have API security to avoid data breaches and unauthorized access.
API Security Measures:
- Use OAuth 2.0 and OpenID Connect to securely authenticate.
- Use rate limiting and API gateways to avoid abuse.
- Use TLS 1.3 to encrypt data being sent over APIs.
Why It’s Important:
Unsecured APIs have become a major attack vector for hackers. Attackers use vulnerabilities in the API to exfiltrate sensitive information or take down services. Businesses can guard against unauthorized entry and data theft by using strong authentication, access controls, and encryption.
5. Implement Advanced Threat Detection and Response
SaaS applications need to use AI-driven threat detection and real-time monitoring to effectively counter cyber attacks.
Key Technologies:
- Security Information and Event Management (SIEM) solutions for security log analysis.
- Extended Detection and Response (XDR) solutions to counter threats in real-time.
- Behavioral analytics to identify insider threats and anomalies.
Why It’s Important:
Cyber threats are becoming more sophisticated nowadays, rendering conventional security measures ineffective. AI-powered threat detection enables organizations to identify advanced attacks in real-time and react accordingly. This decreases response time and reduces potential damage from cyber attacks.
Protect your SaaS business from cyber threats now.
6. Strengthen Data Encryption and Privacy Controls
Businesses should apply strong data encryption methods for SaaS applications to maintain data confidentiality and integrity.
Best Encryption Practices:
- Encrypt the data at rest and during transit with AES-256 encryption.
- Enforce end-to-end encryption (E2EE) on sensitive communication.
- Comply with global data privacy regulations (GDPR, CCPA, HIPAA, etc.).
Why It’s Important:
Data breaches can be disastrous, causing financial loss and damage to reputation. Encryption is a vital defense because it makes data unreadable even in case of compromise by unauthorized parties. SaaS providers also need to have strong SaaS Identity and Access Management (IAM) solutions to protect encryption keys and prevent the use of unauthorized access.
7. Implement Role-Based Access Control (RBAC) and Least Privilege Access
Limiting access to sensitive information is important in order to reduce insider threats and unauthorized changes.
Access Control Best Practices:
- Utilize RBAC for allocating user roles according to job functions.
- Utilize Just-in-Time (JIT) access to restrict excess permissions.
- Periodically review and remove unnecessary access permissions.
Why It’s Important:
Insider threats, both intentional and unintentional, represent a security risk. By implementing RBAC and least privilege access, organizations can help ensure that applications and employees only see the data they need to perform their roles. This avoids exposing data unauthorisedly and reduces the scope of a possible security breach.
8. Regularly Backup and Implement a Recovery Plan
Cyberattacks such as ransomware can lock organizations out of their SaaS applications. Frequent backups and a disaster recovery strategy of SaaS security services ensure business continuity.
Best Practices:
- Automate backups for SaaS application data.
- Store backups in multiple locations (on-premise and cloud).
- Test disaster recovery plans regularly to ensure quick recovery.
Why It’s Important:
Ransomware attacks have increased recently, targeting businesses of every size. Having a good backup and recovery plan means that businesses will be able to recover quickly without needing to pay ransom requirements. Businesses should also perform practice disaster recovery exercises to test their readiness.
9. Educate Employees on SaaS Security Best Practices
Human mistake is still one of the largest cyber security risks. Ongoing cyber security awareness training mitigates against social engineering attacks.
Training Topics:
- Phishing attack prevention
- Safe password practices
- Secure use of SaaS applications
- Incident reporting procedures
Why It’s Important:
Employees are typically the weakest point in terms of cybersecurity. Phishing and social engineering attacks are commonly used by attackers to trick employees into revealing credentials or installing malware.
10. Ensure Compliance with Regulatory and Industry Standards
SaaS application development service providers need to comply with global security frameworks to ensure trust and compliance.
Major Compliance Frameworks:
- ISO 27001 (Information Security Management)
- SOC 2 (Security, Availability, and Privacy controls)
- GDPR & CCPA (Data privacy and protection laws)
- HIPAA (For healthcare SaaS applications)
Why It’s Important:
Regulatory compliance is not just about avoiding fines; it builds customer trust and ensures robust security measures are in place. Businesses must stay updated on evolving security laws and implement controls to meet industry standards. Conducting regular compliance audits can help identify and fix gaps proactively.
Compliance is not merely about staying out of fines; it generates customer confidence and provides solid security measures. Companies need to keep themselves informed regarding changing security legislation and introduce controls to achieve sector standards. Having compliance audits run regularly can assist in detecting and resolving gaps ahead of time.
Conclusion
In 2025, SaaS application cybersecurity threats will still be in a continuous evolution mode and need proactive and futuristic security solutions. Zero Trust Security, MFA, API security, advanced threat detection, and robust encryption need to be embraced by organizations for safeguarding their SaaS application development environments. With these best practices in place, companies can reduce risks, ensure compliance, and keep their data secure in a more digitalized world.
At Triveni Global Software Services, we are committed to integrating cutting-edge security measures into our SaaS development services, helping businesses build resilient and secure applications for the future.
FAQS
You can Secure the SaaS application by using a multi-layered security approach. That helps to incorporate robust encryption, Multi-Factor Authentication (MFA), continuous monitoring, access control measures (like Role-Based Access Control or RBAC), and routine security auditing. This can ensure data privacy compliance and keep software up-to-date.
The 5 security essentials of the SaaS model are:
- Data Encryption: Encrypt data both at rest and in transit to secure sensitive data.
- Identity and Access Management (IAM): Securely control who can access your application using strong authentication methods.
- Regular Security Audits: Regularly scan for vulnerabilities and maintain compliance.
- Incident Response Plan: Have a response plan in place for suspected breaches.
- Compliance and Regulatory Standards: Adhere to relevant industry regulations such as GDPR, HIPAA, and SOC 2.
SaaS application development is the process of developing cloud-based software applications that are hosted via Internet. Users have access to these apps through a subscription-based model, without having to deal with infrastructure. SaaS applications are generally developed with scalability, security, and multi-tenant architecture in mind so that providers can serve several customers easily.
The top 5 emerging trends in cyber security include:
- Zero Trust Security: The “never trust, always verify” mechanism to provide secure access control.
- AI and Machine Learning: Using AI to anticipate and identify cyber threats in real-time.
- Cloud Security: Securing cloud-based infrastructure as more companies shift to the cloud.
- Extended Detection and Response (XDR): Consider Advanced solutions that offer more visibility and response for multiple environments.
- Ransomware Defense: Enhanced methods and tools to identify, block, and contain ransomware attacks.
The newest technologies in cyber security are:
- AI and Machine Learning: This technology is for predictive threat identification and automated response to security threats.
- Behavioral Analytics: Detecting abnormal patterns in user behavior to identify threats.
- Quantum Cryptography: Applying quantum computing for enhanced encryption.
- Extended Detection and Response (XDR): Unified security products that offer full protection on endpoints, networks, and cloud infrastructure.
- Security Automation: Tools and platforms that automate mundane security processes, enhancing efficiency and speed of response.